Azure Bastion
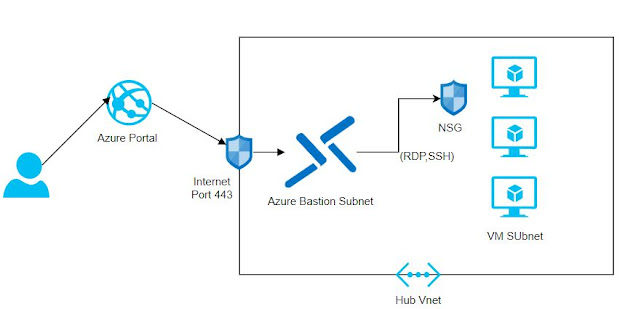
Azure Bastion is a new feature of Azure which allows RDP/SSH connectivity to virtual machines directly in the Azure portal over SSL and without any public IP on your virtual machines.
Subnet name must be AzureBastionSubnet and it should be in same address space as VM created . I have placed my VM's and Bastion in Linux-Vnet
Facts about Bastion:
- It is a PaaS service which provides RDP/SSH connectivity for VM running in azure using SSL without need of Public IP
- Azure Bastion and VM's should be provisioned in same Vnet
- Connect to Azure Portal over HTTPS and then select the VM you wanted to access
- Azure Bastion has public IP which will be used by Azure management portal to provide RDP/SSH over SSL (443) . We cannot SSH or RDP the Bastion Public IP.
- New session in browser open and provides access to VM you wanted to connect.
- It is like a gateway that you use to connect the VM using a browser and in return you get RDP/SSH session of the VM
How to Configure Bastion:
Bastion can be configured through Powershell, CLI & GUI. Am using GUI method to create the service.
Public IP created will be used for SSL connectivity
How to connect :
Key in the Username and upload the SSH key pair for VM hit connect. VM session opens in the browser.
If you like to harden the Bastion with NSG add below Inbound & Outbound rules.
Inbound Rules:
Outbound Rules:
Source:
https://docs.microsoft.com/en-us/azure/bastion/bastion-nsg
https://azure.microsoft.com/en-us/blog/announcing-the-preview-of-microsoft-azure-bastion/





0 comments:
Post a Comment